OK, first and foremost I owe GFI an apology. They had asked (nicely) if I would review their end point security product and I said I would do so happily. Now, that was over a month ago. So, for that I do apologize.
One of the ongoing struggles that people tend to have in IT is the USB storage device. Be it a thumb drive, iPod or what have you, there are varying degrees of alarm. My Motorola RAZR phone for example works as a USB storage device. How often would a security guard seize a cell phone while entering a government installation? I know that many of the DC offices that I worked in never once challenged my cell phone. For USB, it really all depends on your policy set that you are working from. Here is an excerpt from a reader’s email discussing how to monitor USB on their network.
As for the USB, the problem I have is that there is a legitimate business need. We need to transfer large files (>1 GB) to a client on a regular basis. (snip) so we’re stuck moving the files on media via courier. The client computers do not have DVD players so we can’t use those either. At least these will be single use USB Drives never to return to our building.
The frustration is apparent. This provides a nice segue into the GFI product offering, EndPointSecurity. This product comes in two flavours. The first is a web based scan that leverages an OCX to scan your network. For the love of anything holy do not do this unless you have permission. I cannot emphasize that enough. Warning aside this provides small IT shops the ability to check their networks with this free web based utility. Give it a whirl on your lab/home system. The real draw for me is the application itself rather than the web based approach.
When we download the binary version we first off run the EULA through the analysis.
7. CONSENT TO USE OF DATA.
You agree that GFI SOFTWARE Ltd. and its affiliates may collect and use technical information you provide as a part of support services related to the Product.8. GFI SOFTWARE Ltd.
agrees not to use this information in a form that personally identifies you.
Er, OK. Fairly standard. No other huge surprises in the EULA.
Next up on the install process you have the option to run this as ‘system’ or you can tailor it with the account of your choosing. As well, you can pick and choose the types of USB devices that you want to control.
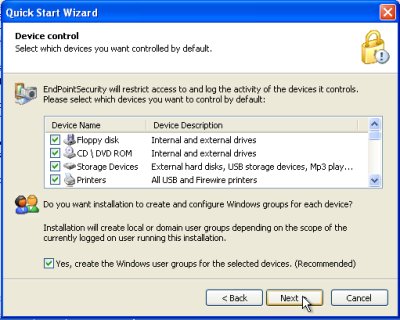
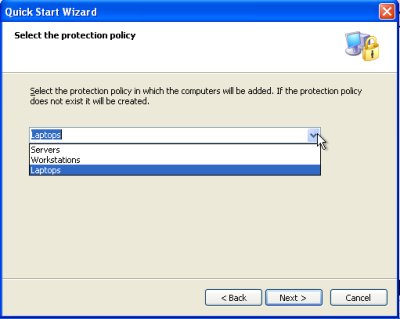
Once the install has completed there is a handy wizard to walk you through the initial setup. It has three default policies that you can select from (servers, laptops, workstations)
Once loaded here is what the application should look like. Mind you I have only loaded one virtual machine into the mix so your layout will most likely appear differently.
Next up you will need to right click on the node that you woulld like to protect and select deploy.
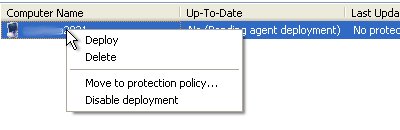
Now, assuming the you have write access to the node that you are attempting to protect (and the firewall will permit access) you should receive this message.
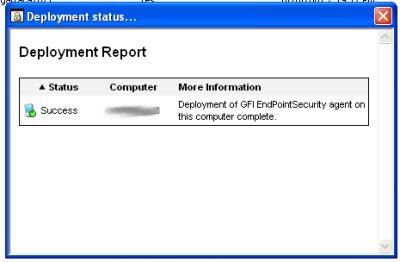
An excellent and easy to use offering from GFI. I suggest that you try it yourself. There is a 30 day trial version that is available for download. I recommend giving it a test drive.
[tags]GFI EndPointSecurity, GFI, USB Devices, iPod Discovery, End Point Security, Tools[/tags]


