
Security is an interesting thing. Some people get it. Others just have no idea. A few days ago Myrcurial found that a DHS document had been erroneously posted on the Water ISAC site. Mistakes happen lets be fair. But, rather than say “Yup, we goofed. It won’t happen again and here’s why” the rather apt description of the Keystone fellas reared its head, again.
An email was sent out on the SCADA security mailing list instructing folks to cease talking about this issue (thx to anonymous for the copy).
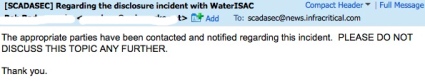
So, being a curious sort I went to the publicly accessible archive to view the message thread so I could catch up on the story.
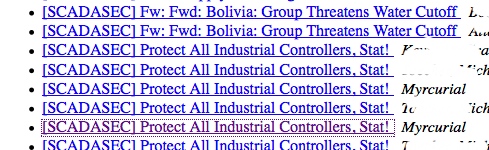
Only to discover that any message relating to the document posting was now deleted. Guess they might have forgotten that every subscriber on the list also has a copy.
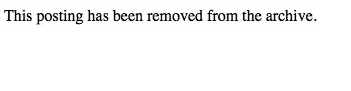
How can one ever hope to have a frank and open discussion about security in the critical infrastructure space when the default action is to close your eyes and bury your head in the sand?
Anyway. So, I decided to go have a look at the archived document on Google. Nope, not there anymore. Guess someone had Google take the link down. Well, that showed me.
Or did it?
Oh right, there are other search engines besides Google. You might of heard of some of them like say a small little site called Yahoo?
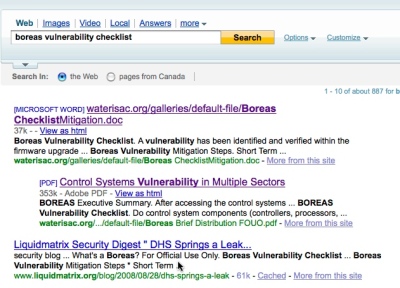
Yup, they have an archived copy as well. As will the rest of the search engines out there.

What’s the moral of the story? Once the genie is out of the bottle on the internet there really is no way to get that sucker back in. As our readership from the various three lettered agencies can attest.
WaterISAC and other organizations that have critical infrastructure roles really need to review their document classifications and how things get published to the web. Seriously, this isn’t rocket science. Be a little more careful next time folks.
Oh, and WaterISAC, please turn off directory browsing on your web server.
[tags]WaterISAC, FOUO, DHS, security advisory, boreas[/tags]



Here is an email that was deleted that you might be interested in.
(start)
We, the moderators of SCADASEC, wish to remind everyone that this list is
NOT for the discussion of specifics of any industrial, IT, SCADA, or control
system vulnerabilities. Others can take that box of dynamite and play with
it at their own risk. We choose not to go there.
This list was created for the discussion of the background behind these
vulnerabilities. How does one deal with them in a timely fashion? What are
the risks of various information distribution methods? Can we categorize a
vulnerability in a way that might make disclosure issues easier to determine
and understand? What roles and responsibilities does a researcher, a
software maintainer, an end-user, an integrator, an engineer, or a C-level
executive have? Where should government fit in? How do regulations impact
these issues? And so on and so forth…
Remember is that this is an open list. We do not know who reads it. We have
engineers, researchers, software writers, government, and many others
represented here; and that probably includes at least a smattering of hackers,
red teams, and intelligence agencies. We formed this list because we feel
that there is not much consensus on how to deal with Industrial Control
System Security issues. We will not discuss specifics regarding security
leaks, though background issues surrounding the leak, the ethics, and the
response to the leak are fair game.
(end)