Akamai’s Prolexic Security Engineering and Research Team (PLXsert) is tracking the spread of Spike, a new malware toolkit that poses a threat to embedded devices, as well as Linux and Windows systems.
Several versions of Spike can communicate and execute commands to infected Windows, desktop Linux and ARM-based devices running the Linux operating system (OS), PLXsert said in an advisory Wednesday morning.
From the advisory:
Binary payloads from this toolkit are dropped and executed after the successful compromise of targeted devices, which may include PCs, servers, routers, Internet of Things (IoT) devices (i.e., smart thermostat systems and washer/dryers) and home-based customer premises equipment (CPE) routing devices.
The toolkit has multiple DDoS payloads, including SYN flood, UDP flood, Domain Name System (DNS) query flood, and GET floods. Several campaigns have been reported against hosts in Asia and the U.S.1 Several Akamai customers have been targeted by DDoS attack campaigns launched from this botnet. One attack peaked at 215 gigabits per second (Gbps) and 150 million packets per second (Mpps).
There are several ways to tell if your systems have been infected by this toolkit.
“Principal indicators of infection are the presence of a series of binaries that infect specific operating systems and architectures,†the advisory said. “PLXsert analyzed binary payloads associated with the Spike DDoS toolkit that targeted desktop Linux OSs and ARM-based Linux hosts. Russian anti-virus company Doctor Web also reported on what may be iterations of the toolkit, and evidence of the payloads being ported to Windows has surfaced.2 The binaries associated with the Spike DDoS toolkit consists of one binary, while the iterations found by DrWeb may include several different binaries and other scripts associated with an infection.â€
The toolkit is not particularly unique. It has the hallmarks of a garden-variety botnet, with a command-and-control panel, binary payloads and DDoS payload builders. Spike’s ability to produce ARM-based payloads suggests the creators are after routers and loT devices to hijack into their botnets. The advisory calls this part of the “Post-PC Era†of botnet proliferation.
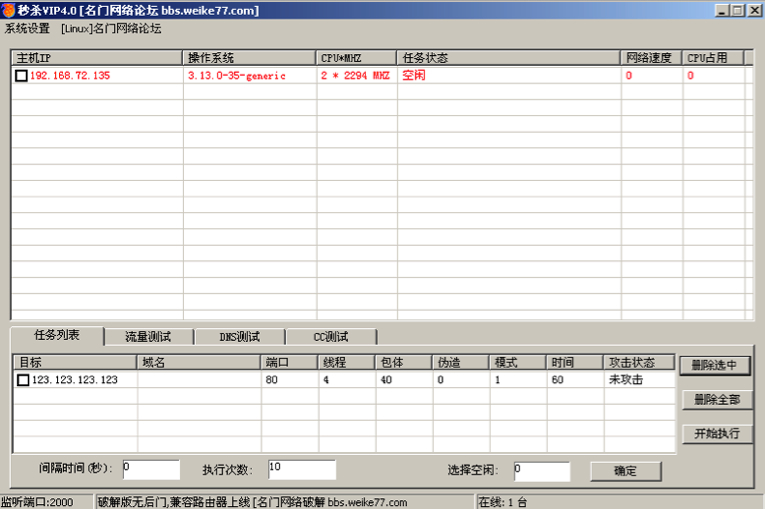
The C2 panel contains a fairly basic interface written in Mandarin Chinese.
The multi-architecture malware code found in this kit increases the threat’s complexity and sophistication and makes it necessary to apply hardening measures to each of the targeted operating systems and platforms. The following organizations provide guidance for system hardening:
- SANS Institute checklist for Linux server hardening
- Microsoft list of baseline Windows hardening guidelines to secure windows servers
- The National Security Agency guidelines for securing various operating systems
- Tripwire security recommendations for small office, home office (SOHO) routers
- NIST guide to secure mobile devices in the enterprise
- University of Michigan guide to securing and managing Android security phones/tablet
- OWASP list of the 10 most critical Internet of Things (IoT) security risks
IT security practitioners can also use the open-source YARA tool to find and classify Spike-related threats.
You can download the full advisory here.