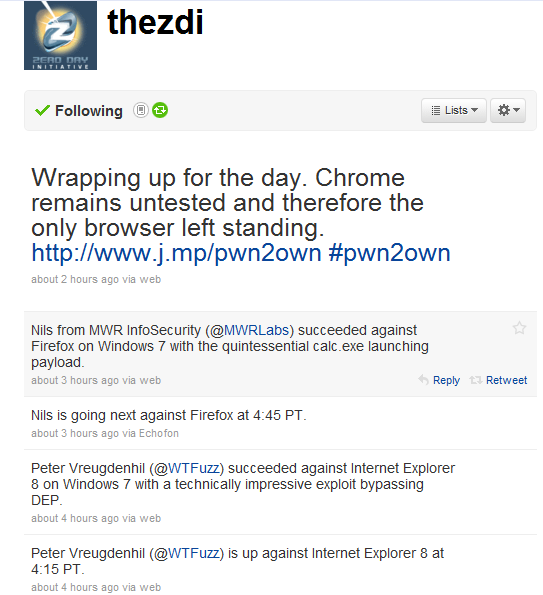
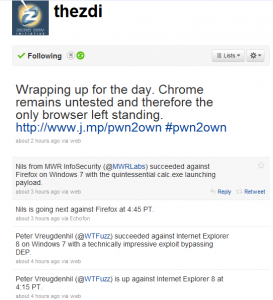
Everybody had high expectations for this year’s Pwn2Own but I think I speak for more than just myself in saying that today blew me away. All browsers tested were successfully exploited with a bonus iPhone exploit. The only browser left standing is Chrome and that is only because it hasn’t been tested yet, and based on today’s success rates I would expect more from tomorrow.
First off, Internet Explorer 8 running on a fully patched 64-bit Windows 7 system was successfully taken down by a Dutch hacker by the name of Peter Vreugdenhil. This exploit was especially interesting because it bypassed ASLR (Address Space Layout Randomization) and DEP (Data Execution Prevention) which by all standards is very impressive.
“Despite what happened at #pwn2own, I have never seen any mass malware evade even DEP by itself.” Comes from a security researcher who I didn’t ask permission to name so I’ll omit, but definitely interesting.
If you want to read more from Vreugdenhil about this exploit you can read the PDF he published.
Next, a less surprising but no less impressive successful exploit comes from Charlie Miller against a Macbook via Safari for the third year in a row. Miller set up a website containing an exploit the details of which are being withheld until Apple can be notified and address the issue. A conference organizer than surfed to the website and sat back while Miller took full access of the Macbook.
Thirdly, we hop back to Windows 7 but this time our door is Firefox 3 by a German hacker who goes by ‘Nils’. This is the second year in a row that Nils has conquered Firefox and even though the details of the exploit are under lock he did hint towards it was an implementation flaw on Mozilla’s end saying they can do a better job of utilizing ASLR. This exploit also impressively used some general trickery to bypass ASLR and DEP.
Last but not least and probably going to grab the most media coverage is a previously unknown vulnerability in Apple’s widely popular iPhone. The pair of hackers, Vincenzo Iozzo and Ralf Philipp Weinmann, set up a website housing the exploit which, reportedly, took under 20 seconds to dump the entire SMS database of the phone including texts that had all ready been deleted.
For real time coverage of the rest of this event and more reading on each topic you can surf over to ZDI’s twitter page @thezdi or over at the contest overview at TippingPoint | DVLabs.